State Of Software Security 2024
State Of Software Security 2024
I attended a webinar from Veracode last night, which was interesting and made me want to download the fully report and write about it here.
We use Veracode at NIPO. It’s a static code analysis tool.
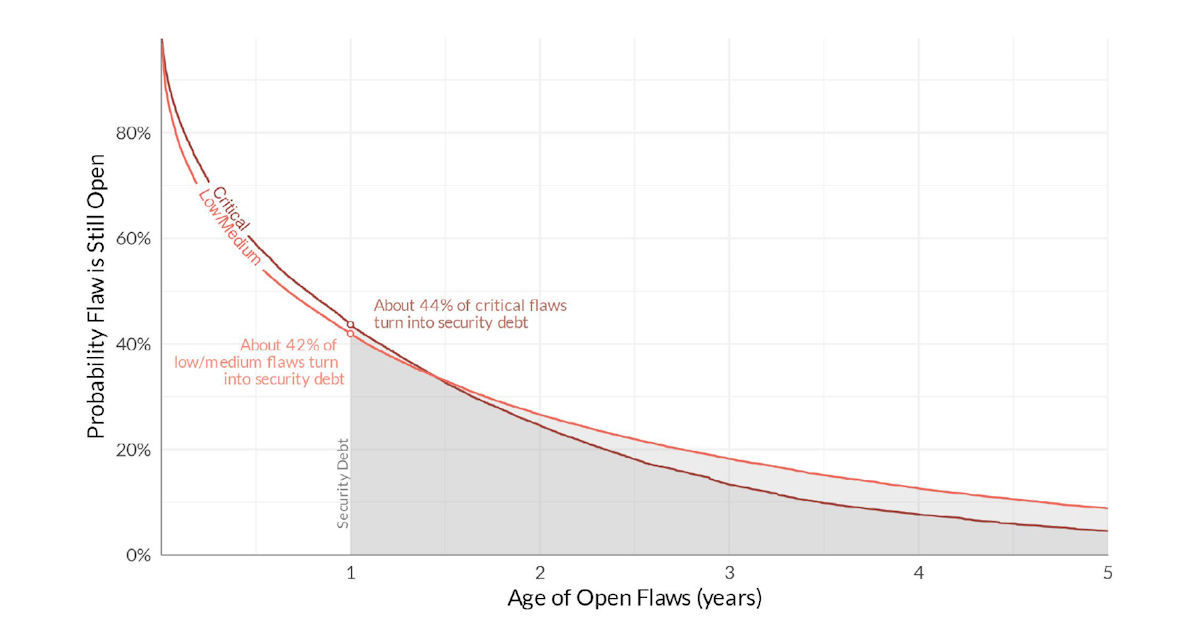
I won’t repeat the whole report here - I recommend you to read it yourself. They define security debt as security flaws that are known but not fixed for more than a year. Here are my main takeaways:
- 63% of applications have flaws in first-party code. 70% have flaws in third-party code.
- 90% of all security debt is in first-part code, but 65% of critical flaws are in third-party code.
- 64% of applications have capacity to fix all critical security debt, which highlights the need for prioritisation. But there is no difference in the rate of fixing critical flaws compared to the rate of fixing all flaws.
- 70-95% of applications use open source libraries that are maintained by a single developer (that’s not really related to security, but an interesting confirmation).
This post is licensed under
CC BY 4.0
by the author.